
Our solution for VoIP security is based on the best of #BigData, #SIEM and Analytics. We collect traffic samples, logs and data. We analyze the data in real-time and provide real-time policy updates to block DoS attacks and fraud early. Data is collected centrally at cloud to provide broadest possible basis for analysis. To guarantee privacy to our customers, all data comes to our cloud service encrypted in a way we cannot decrypt.
COLLECTION
ANALYSIS
REAL-TIME FEEDBACK
VoIP AaaS and SIEM

DATA COLLECTION
Knowledge is power. We tap various sources: our customer's network for specific information, our honeynet for proactive problem detection, and other third-party sources.
Did You Know?
BigData. Even under normal operational circumstances, 1000 subscribers to a public SIP service generate 3 GB raw signaling data a day.
ANALYTICS
Finding harmful traffic is like looking for a needle in a haystack. Our experience shows that an average user of a public SIP service generates 3 MB of signalling a day. Therefore we process, aggregate and analyze the data to find out offending outliers. Administrators and end-users can see their history at any point of time and provide feedback to further refine the security policies.
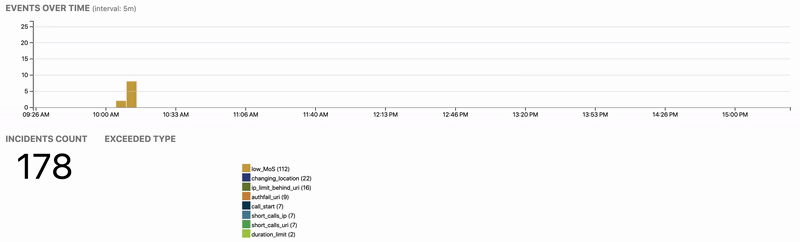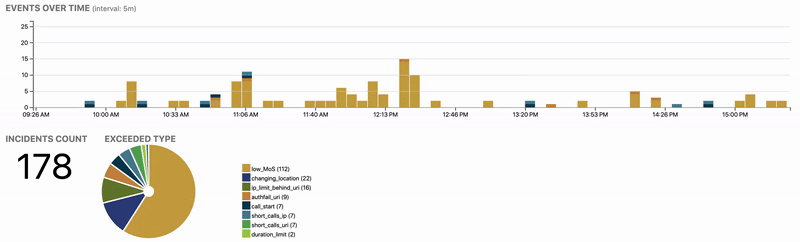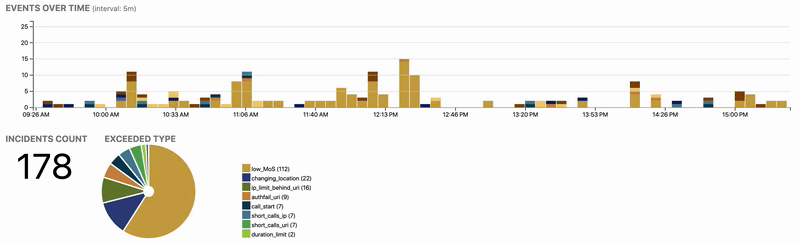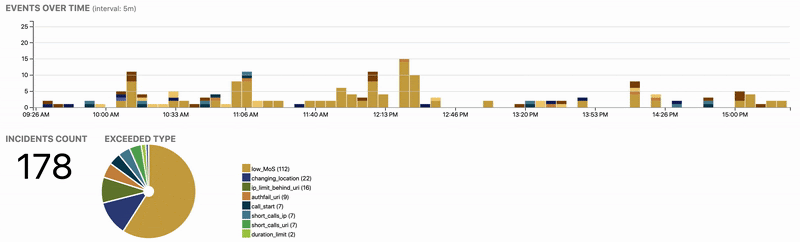
Even if some security equipment is already in place, such as SBCs, Analytics permits to audit their function and achieve compliance with security standards.
Did You Know?
CAIDA reported already in 2011 on the SIP sality botnet attack that originated from *three million* distinct IP addresses.
BLOCK ROUND THE CLOCK
Human responders can't keep pace with attackers, botnets and automated penetration tools. That's why we automate the response and block offending sources as soon as our analytical processes have identified them. Attack success chance grows dramatically with time and that's where our automated response comes in and blocks offending traffic before it is too late. We can block the traffic even at the network edge so that even other security appliances such as Session Border Controllers are spared overload conditions.
Did You Know?
Europol and CFCA estimated in 2019 telecom fraud to be EUR 29 billion a year. A dictionary password attack at rate of 100 attempts per second finds an Oxford English Dictionary password in less than an hour.
10:45
10:46
10:47
Scanners Omnipresent
Two minutes from a fresh start till first scan appear.
6:15
6:16
6:17
Response Time Matters
40 password quessing attempts per second take 90 minutes to complete Oxford Advanced Learner's Dictionary.

Many Penetration CLI Available
sipcli, sipvicious, sipsak spotted most often

Most Attacks Identifiable Using SIP Analytics
This dial-out scan features a high call attempt failure, a single source adress and predictable call patterns.